Struggling with access sprawl or security gaps? Role-Based Access Control (RBAC) ensures the right users have the right permissions - no more, no less.
Our RBAC Matrix Template transforms chaotic access management into a structured system, reducing risk and operational overhead.
Why basic permissions aren’t enough
Ad-hoc access assignments lead to:
- Security vulnerabilities (overprivileged users = breach risks).
- Compliance failures (audits flagging improper access).
- Operational delays (IT drowning in permission requests).
Our template replaces guesswork with a scalable framework, aligning access with business needs.
The 4 core components of the RBAC matrix template
An effective RBAC system hinges on four foundational elements. Our RBAC matrix template cuts through the complexity, turning access control from a reactive chore into a proactive strategy.
1. Role definitions
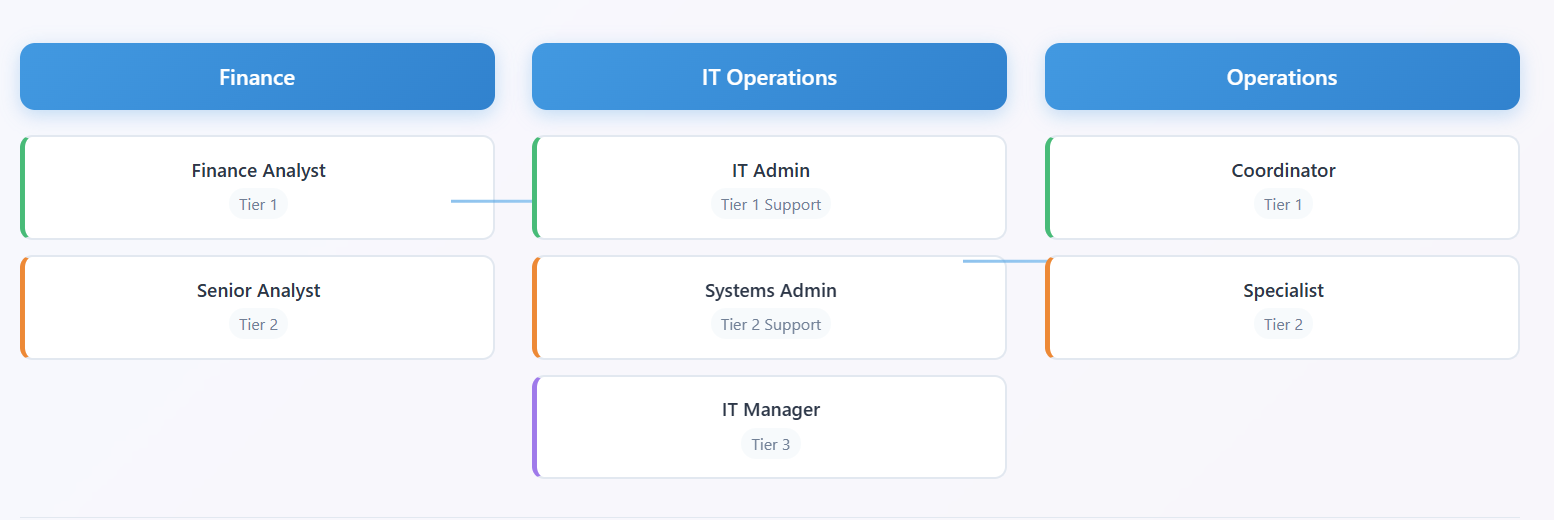
Clarity over confusion. Map job functions to standardized roles (e.g., "Finance Analyst," "IT Admin").
- Role titles & descriptions
- Cross-functional team alignment
- Hierarchy (e.g., Tier 1 vs. Tier 2 Support)
2. Permission mapping
Least privilege, enforced. Define exact access rights per role.
- Systems/applications covered (e.g., ERP, CRM, DART)
- Permissions granularity (view/edit/admin/delete)
- Exception handling process
3. User assignment
Achieve audit-ready accountability. Track who holds which roles.
- User-to-role assignments
- Approval workflows
- Temporary access expiration
4. Review & compliance
Gain proactive control. Ensure permissions stay current.
- Quarterly access reviews
- Role-change triggers (promotions/offboarding)
- Audit trail documentation
Optimizing your RBAC implementation: Best practices for success
To maximize the effectiveness of your Role-Based Access Control framework, follow these best practices to ensure seamless adoption, compliance, and long-term scalability:
1. Adopt a phased rollout approach
Begin with a controlled implementation by piloting RBAC within high-risk departments such as Finance, IT, or Legal. This allows you to refine role definitions, identify potential gaps, and gather feedback before expanding across the entire organization.
2. Leverage automation for efficiency
Manual role assignments are time-consuming and prone to errors. Integrate Dart with HR systems to automate user provisioning. This ensures that access rights are dynamically updated based on employment status, role changes, or department transfers.
3. Centralize documentation for compliance & audits
Maintain a comprehensive, up-to-date RBAC repository that serves as the single source of truth for permissions, role hierarchies, and approval workflows. Detailed documentation not only simplifies internal audits but also ensures compliance with ethical standards, such as GDPR.
4. Educate teams on role governance
Stakeholder buy-in is critical for RBAC success. Conduct training sessions for managers and department heads to clarify role boundaries, approval processes, and exception protocols. Well-informed teams will make fewer ad-hoc access requests.
The impact of a structured RBAC
Organizations that adopt a structured Role-Based Access Control matrix often see tangible improvements across security, compliance, and operational efficiency.
- ✅ 50% fewer access-related breaches
With clearly defined roles and permissions, overprivileged accounts become a thing of the past. By enforcing least-privilege access, security teams can prevent accidental data exposure and reduce the risk of insider threats.
- ✅ 30% faster compliance audits
A well-documented RBAC matrix makes audit preparation faster and more accurate. Auditors can easily trace user access, understand permission logic, and verify that appropriate controls are in place, eliminating the scramble to pull reports last minute.
- ✅ Reduced IT ticket volume for access requests
When users are assigned roles with predefined permissions, there’s no need to submit ad-hoc access tickets. This not only lightens the load on IT and security teams, but also speeds up onboarding and internal transfers.
Beyond metrics, structured RBAC also improves internal confidence. Business leaders gain visibility into who has access to what, while teams feel more empowered with the access they need, without unnecessary delays or security risks.
Stop risking security gaps
Implementing a structured RBAC Matrix is the key to balancing security, efficiency, and compliance in your organization. By defining clear roles, automating permissions, and conducting regular reviews, you’ll reduce risk, streamline operations, and ensure audit-ready access controls.
Don’t let outdated or overly permissive access policies expose your business to vulnerabilities. Download our template today!







